Cyberuptive Security Operations Center (SOC) responded to an alert for a suspicious AutoIT execution on a system used by a system administrator AKA sysadmin. The Cyberuptive SOC investigated the alert, determining the system had been compromised, and subsequently contained the system from the network. Cyberuptive assesses with moderate confidence the adversary crafted and purchased malicious advertisements (malvertisements) on Bing and possibly other search engines for a tool popular with sysadmins. Endpoints used by sysadmins are of particular interest to adversaries because they are often where credentials to the enterprise network AKA “keys to the kingdom” are used and stored. Read on for more details about what came before, and after, the suspicious AutoIT alert.
The investigation revealed the computer user had downloaded what purported to be Advanced IP Scanner, an otherwise legitimate tool from a legitimate company.
Except…
While it wasn’t a legitimate tool, and it was not from a legitimate site, the “Official” tag displayed by Bing triggered the assumption that the search provider performed some vetting to determine the legitimacy of the result (Figure 1).
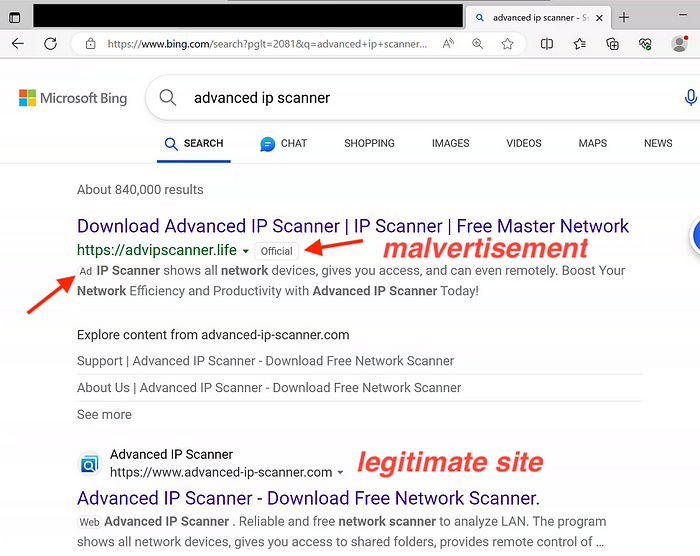
URL history showed the ultimate source of the downloaded file is Dropbox (Figure 2), which is practically unheard of for legitimate, widely distributed applications, but common for malware because of anonymity provided by Dropbox’s “freemium” tier.
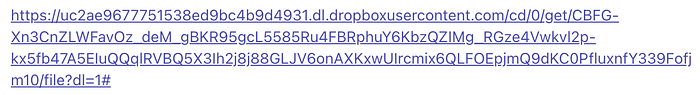
Figure 3 shows the downloaded file as viewed in Windows Explorer.

Cyberuptive SOC analysts were not the only ones analyzing this file. On 03 August 2023, netizens from Cokato, Minnesota USA and Warsaw, Poland uploaded this same file to the online malware repository VirusTotal, to check against more than 60 antivirus vendors. Only one of those antivirus vendors detected the file as malicious (Figure 4).

Cyberuptive decrypted the malvertisement browser redirect chain to a subsequent malicious payload and identified the possible API key of the malicious Bing advertiser in Figure 5.

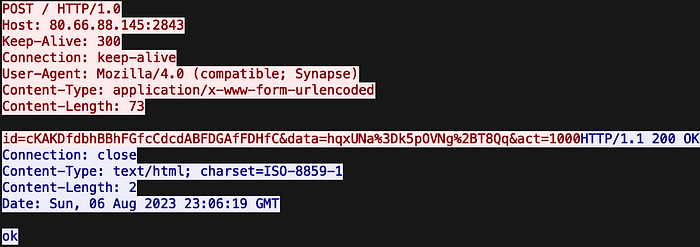
While too small in size to be the legitimate Advanced IP Scanner tool, when executed interactively on a live sandbox system it did indeed go out and fetch a copy of the legitimate Advanced IP Scanner. However, the latter was effectively unusable by the user because it ran in the background outside of the Windows interface. At the same time, the Microsoft Installer (MSI) extracted and launched the payload that it had brought with it inside. Cyberuptive determined the malware payload inside is DarkGate. DarkGate has crypto mining, credential and key stealing and keylogging, and remote control capabilities. Figure 6 shows the initial command and control (C2) beacon of a system infected with DarkGate from this malvertisement campaign.
Several days before this post, researchers at Aon described this DarkGate malware, with a focus on the keylogging function. Based on overlap in tactics, Cyberuptive believes the adversary described by Aon is possibly the same adversary as that behind the Bing malvertisement campaign described in this post. Aon links this activity to a financially-motivated adversary known as ScatteredSpider.
While this analyst will save repeating all of the details of the malware as competently analyzed in the post by Aon, a few things are worth pointing out about DarkGate’s evasive nature. DarkGate’s obfuscated AutoIT script does process hollowing and loads malware into a process launched from a random executable already on the system. Using the legitimate process as a wrapper to hide its code from endpoint technology systems is one of multiple evasion techniques to minimize detection. While AutoIT script-based malware has had a reputation among threat researchers as indicative of a poorly resourced malware developer compared to purpose-built code, DarkGate should remind network defenders that AutoIt script-based malware is still relevant in the threat ecosystem and should not be discounted.
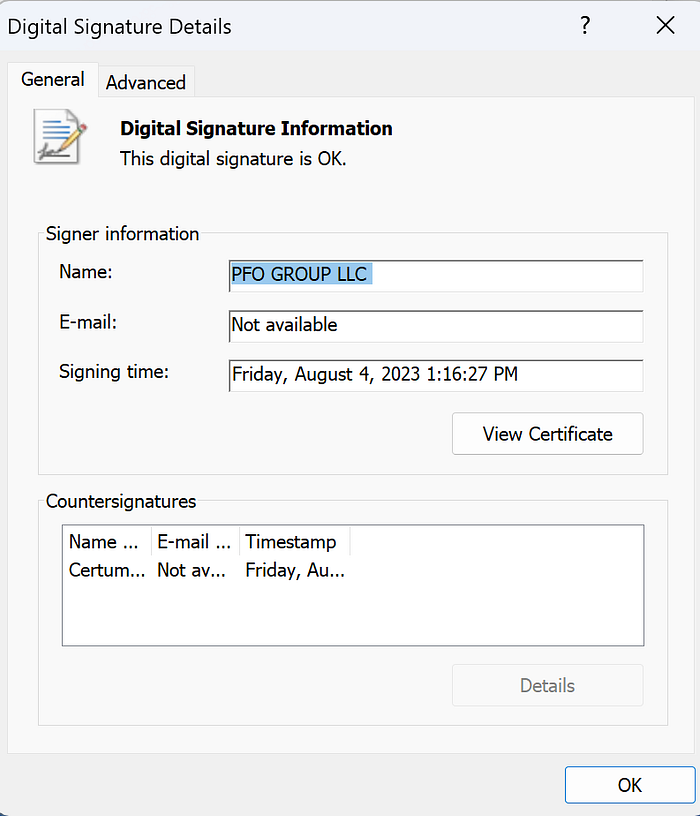
Cyberuptive pivoted from the name of the (likely front) company “PFO GROUP LLC” whose name is in the code-signing certificate for the malvertisement delivered MSI file (Figure 7).
Cyberuptive found nine other samples signed by PFO Group LLC on VirusTotal as of 7 May 2023. All of these files are DarkGate, most impersonating an installation file for Advanced IP Scanner, as well as a few that purport to be an installer for “PYT,” possibly PyTorch for Windows.
In several cases, Cyberuptive was able to recreate the malvertisement delivery chain and download additional DarkGate MSI files such as that screen recorded in Figure 8.
Figure 8— Screen recording of malvertisement and download of DarkGate loader MSI file
The more recently obtained MSI file shown in the screen recording included a legitimate version of Advanced IP Scanner application, likely to use as a more convincing decoy while installing the DarkGate malware in the background. Cyberuptive uploaded the malicious MSI file to VirusTotal which still shows zero detections as of this post time. Cyberuptive also uploaded DarkGate Portable Executable (PE) files that we carved from the memory of an otherwise legitimate process hollowed and injected with the DarkGate malware. Note the drastic difference in detection here and here compared to the DarkGate MSI itself.
Adversary Source Filtering
We noted that the adversary appears to perform source filtering and only delivers the malicious MSI once to an IP address. Repeat “visitors” from the same IP address get directed to a landing page where no downloads are available (Figure 9).
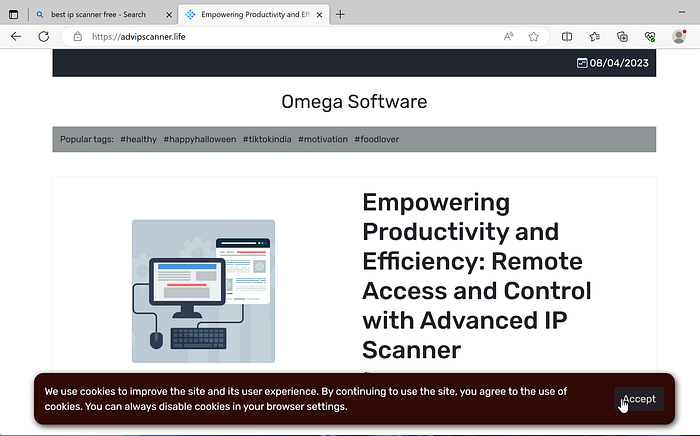
Source filtering of infrastructure associated with Bing automated analysis infrastructure may have allowed the adversary to escape initial detection of their campaign. Cyberuptive notified Bing on 04 August 2023 via their advertisement reporting form and noticed no similar malvertisement after 05 August 2023. We cannot confirm, however, if our notification was responsible for the apparent end of the malvertisement campaign.
Detection and Mitigation
- Retain the service of a competent 24-hour SOC for ongoing monitoring and rapid response to indicators of adversary activity.
- Network defenders should investigate with high priority any indication of AutoIT execution and script loading, especially on networks that do not normally employ AutoIT.
- Consider zero trust architecture to prevent communication with untrusted URLs and adversary C2 hosts, and to prevent download of untrusted applications and executables.
- Absent zero trust architecture, restrict outbound enterprise firewall egress polices to only necessary ports for browser traffic (80 and 443), and allowlist other internet destinations by exception.
- Consider ad blocking technologies and regimes appropriate for the enterprise acceptable risk policy.
- Educate computer users on recognizing malvertisement techniques such as described in this blog post. Only install software from known good and approved application vendor websites or vetted organization repositories, and confirm that the software behaves as expected.
Conclusion
Cyberuptive SOC investigated suspicious AutoIT activity on a system used by a sysadmin, revealing a malicious malvertisement campaign for DarkGate malware installers purporting to be a tool popular with sysadmins. Cyberuptive isolated the compromised system and notified Bing. We are sharing this post with indicators of compromise (IOCs) to bring additional attention to the threat of malvertisement, especially for systems used by sysadmins.
IOCs
advipscanner\.life
ipadvancedscanner\.com
advipscan\.buzz
80.66.88\.145
Hashes
5a5fc342145370818aabfd363234f162
4b742e00b27fd52843ce96db0c330418
4deb1e1221628f9dc0b8650632b2c8e5
b2d5a1369b5b88c18e5123b948683ba8
485064a4e5c78b791e8f1126634ca49d
ec3c95ba898a58b5f118b096acc27f3b
a4a98276009f46ae7ea78eefdf5c49af
8617b78940c3e60af038e3568bdf2c4b
0ae8981e9e1530a85fb3fe91c8343e09
Additional screenshots




